Introduction to ServiceNow Security Incident Response:
ServiceNow Security Incident Response (SIR) allows organizations to automate the process and drastically reduce the speed of the whole security incident response process.
Teams using ServiceNow SIR have access to every tool they require to respond effectively using predesignated time periods, mitigate as much possible harm, and make the response processes easily tractable and auditable.
The Role of Security Incident Response in Modern Cyber Defense:
Security events like phishing, ransomware, insider threats, and malware outbreaks can result in severe interruption, loss of money, and the loss of reputation. Such incidents tend to be handled on ad hoc basis in an uneven way without a proper response system in place.
SIR stands in the middle of supporting security departments:
- Reduction of Mean Time to Detect (MTTD) and Mean Time to respond (MTTR)
- Automate the response processes to be reusable and conformed
- Foster partnership between security and the information technology staff.
- Have a clear view of current threats and performance of resources
- Keep regulator-compliant records to be audit ready
When SIR is incorporated into security operations, organizations will be able to go beyond the manual, reactive mode of operations to more automated and intelligence-based mode.
What is ServiceNow Security Incident Response?
ServiceNow Security Incident Response is a highly integrated application on ServiceNow that helps in finding, investigating, containing, resolving, and documenting cybersecurity incidents.
It integrates with other security tools to consume alerts, provides context about that alert with assets and threat data and makes it easy to work through the problem in a structured manner through automated workflows and shared workspaces.
Key Features of ServiceNow Security Incident Response:
Real-Time Alert Ingestion:
- Consumes SIEM, firewall, EDR product and threat intelligence product alerts
- Automatically creates and reads security events into level of severity and level of business impact
Incident Enrichment:
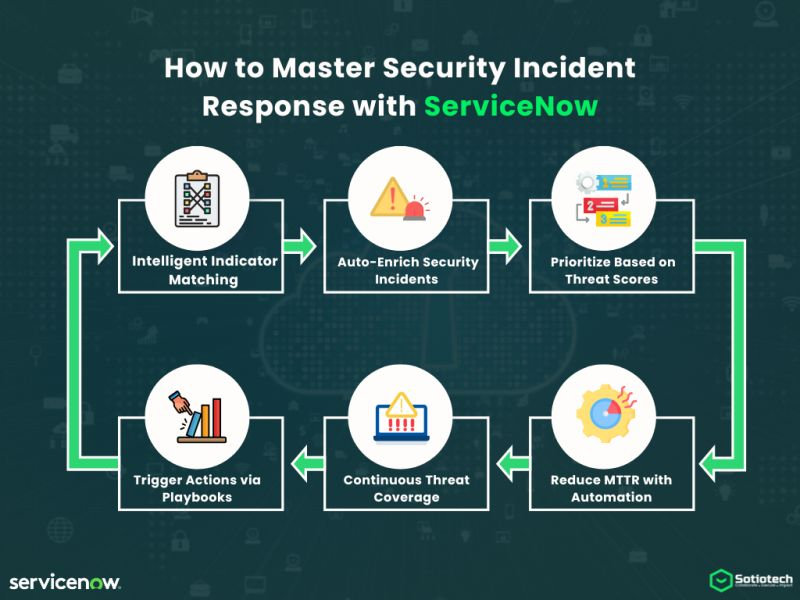
- Enriches the incidents with user identity, asset data, CMDB relationships and IOC-matches
- Allows situational awareness, context, and greater triaging expediency to analysts
Automated response in playbooks :
- The tasks of defining model workflows to be employed in the treatment of type of threats (phishing, malware, ransomware)
- Enables semi-/fully-automated resolution under the supervision of analysts
Dashboards and reporting:
- Live dashboards display the incidence volumes, SLAs, breakdowns of prioritizing, and threat trends
- Reporting is made compliant and visible to the executive through customization
Integrated Collaboration Tools:
- Enables the task to be assigned, escalated and shared comments between the roles of security, IT, and risk
- Makes all the stakeholders aware in one collaborative space
Security Incident Response Lifecycle:
1.Identification:
- The integration of systems sends these alerts to a normalization and logging server as an incident
- First sorting and impact are done through automated correlation and priority scoring
2.Analysis:
- User, device, and threat context are added to the incidents
- Analysts determine the level of severity by the risk score and assets affected, and investigate root cause
3. Containment and Eradication:
- Use playbooks to secure the infected system or even nullify the compromised accounts
- Forensic capture, kill sessions, block bad IP or URL
4. Recovery:
- Get back services that have been affected, verify integrity of the system and enable access to it
- Verify that the threats are eliminated and go back to normal operations as the business continues running
5. Post-Incident Review:
- Reconfigure update rules, SIEM alerts, and response tactics on the basis of findings
- To have a quicker processing of the same incidents in the future, convert learnings into knowledge articles
Benefits of Using ServiceNow Security Incident Response:
Faster response time: Real-time enrichment, automated task routing, and playbooks make containment quicker and reduce delays.
Improved Efficiency: Analysts only have to work in one system and there is no need to go through every tool. The saved time is converted to the increase of capacity and capability of focusing on more hazardous events.
Consistent Processes: Standardized workflows minimize the possibility of a human error and guarantee quality to support best practices and regulatory compliance, including GDPR, HIPAA, and PCI-DSS adherence by the teams.
Enhanced Visibility: Managers monitor SLAs, bottlenecks, and KPIs through real-time dashboards. It helps executive teams have the insights to put first in making investments and staffing capabilities.
Audit Readiness and Compliance: All the actions are recorded and they are transparent and traceable. One can export reports to conduct regulatory audits or to review reports at board levels.
Scalability: It is configurable to a large or a small security team, and is flexible in respect to support of multiple simultaneous incidents. Automation and built-in workflows are used easily to manage the incident volumes.
ServiceNow Security Incident Response Workspace:
Centralized Interface: A single workspace provides added information on all the incident data, tasks, information on the assets and status updates.
Guided Response: Playbooks assist the analyst in step-by-step remediation processes that have conditional logic. Phishing, data leaks and ransomware have different workflows so that they have their ways of resolution.
Live Dashboards: Interactive visuals offer a situational understanding and assists the teams in prioritizing threats. Custom widgets enable teams to observe the trends of breaches, attacks and bottlenecks of resolutions.
Collaboration: Security groups can make comments, assign tasks, and escalate incidents all within the platform that reduces delays of in communications as well as in cross-team collaboration.
SIR integrates well with:
- Configuration Management Database (CMDB): Oversee relationship and business effect
- IT Service Management (ITSM): Associate IT incidents or change with security incidents
- Vulnerability Response: Match the instances with existing vulnerabilities and assign the procedures of patching them
- Asset Management: Rapid identification of the asset ownership, its status and risk level
Time-Saving Tools and Intelligence:
Automated Assignment of Tasks: The incidents are escalated to the appropriate analyst or group depending on severity, workload, or type of incident. This will guarantee that the workloads are balanced and initial responses are quicker.
Indicators of Compromise (IOC) Matching: Match against international and local threat information feeds to determine malicious trends. Identify any other attacks like such and find out whether there are any wider campaigns.
Searching and Filtering: The rich filtering tools give analysts the ability to drill down by type of incidents, assets that have been impacted or even attack vectors.
SLA Monitoring: Timers are also built in to notify teams before SLA is violated to take any redress measure. It sends out alerts to the management when critical thresholds are breached.
Predictive Insights: Machine learning finds patterns and suggests to an analyst areas that should be the subject of specific attention. SIR assists in determining resourcing requirement and response performance as time passes.
How SIR Supports Enterprise Security Strategy:
SIR is a Risk Reducer for Business that gives enhanced threat visibility and response. It enables data-drive decision making, helps to mature the organizations’ security posture and fuels continuous improvement.
Benefits include:
- Less time spent out of service due to less time taken in containment.
- Reduction in strain of resources due to automatization.
- Greater security education between faculties.
- The trends analysis and knowledge sharing will be done to mitigate the threats, proactively.
- Improved capability of prioritizing high-risk incidents and allocation of resources prudently.
Conclusion:
ServiceNow Security Incident Response delivers organizations with a new way of tackling security threat. SIR allows security teams to work more strategically and with greater speed by automating detection and investigation, and facilitating an organized response.
SIR is built on the foundations of visibility, consistency, and integration, serving to assist organizations to minimize risk exposure, as well as keep themselves compliant and continue conducting business amidst advancing cyber challenges. As a burgeoning company or a multinational, implementing ServiceNow SIR provides you with wholeness in dealing with what lies ahead in cybersecurity.
Thank you for taking the time to read our content! We appreciate your interest in SotioTech and look forward to helping you achieve your IT service management goals with our ServiceNow solutions. If you have any questions or need assistance, feel free to reach out to us through our page www.sotiotech.com and our pages. Stay connected with us on LinkedIn for the latest update.





